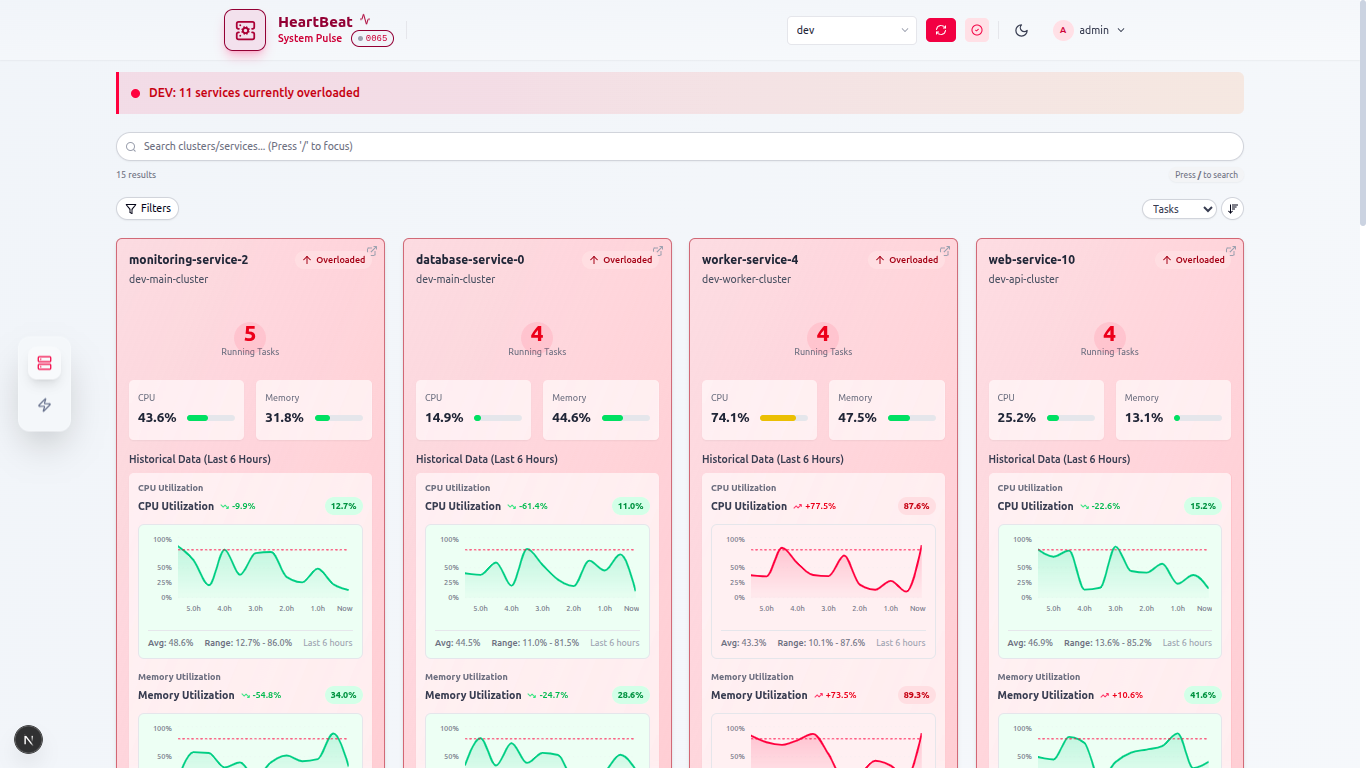
Heartbeat Portal — Unified ECS Observability
/2025A platform-first observability portal that provides zero-click visibility into ECS workloads across environments.
Designing resilience for complex cloud ecosystems.
Target: AWS • GCP • Kubernetes • Terraform
"I work at the intersection of logic and art.
Where stability meets the chaos of innovation."

DevOps Architect · Platform Engineer
I work at the intersection of structure and imagination — delivering systems that scale without chaos.
I am a DevOps Architect and SRE who believes that hope is not a strategy. I build systems that sleep at night so you can too.
My approach is defined by the YogX Philosophy: balancing the rigid discipline of infrastructure stability (Axis X) with the creative chaos of innovation (Axis Y).
"I don't just fix servers; I engineer the platforms that allow products to scale from 'Hello World' to millions of users without breaking a sweat."

Predictable infrastructure via Terraform & IaC.
Curiosity-driven automation that eliminates toil.
Zero-trust architecture baked in, not bolted on.
Measure twice, deploy once. Precision engineering.
Deep expertise in bringing IaC ecosystems to life.
From legacy EC2 migrations to serverless Fargate and air-gapped K8s.
Building the 'OCD' engines that replace manual DevOps work.
Curiosity-driven monitoring portals and production-grade alerting.
Primary Email Channel
yogeshpatil6717@gmail.com
Operational Base Location
Surat, Gujarat, India
Primary Phone Channel
9727707949